[Updated] Security Breach: Latest Risks And How To Stay Safe
In an age where digital vulnerabilities are constantly exploited, are we truly prepared for the next wave of cyberattacks? The relentless march of data breaches, impacting individuals, organizations, and even national security, demands a critical reassessment of our defensive strategies.
The specter of a compromised digital landscape has become a chilling reality. On March 24, 2025, a piece published by Goldberg in The Atlantic brought a specific instance into sharp focus: a security breach linked to a group chat. The article, echoing the anxieties of security experts, raised concerns about the use of platforms like Signal for coordinating sensitive national security operations. This situation, highlighting the potential for violations of the Espionage Act, underscores the delicate balance between technological convenience and the imperative of safeguarding classified information.
The choice of Signal, a platform not explicitly approved for government use in handling classified data, opens up a Pandora's Box of potential risks. The very nature of such a platform, with its encryption features and emphasis on privacy, contrasts starkly with the stringent security protocols required for the handling of sensitive government secrets. Any security lapse, even a minor one, in such a setting could have far-reaching consequences.
The subsequent investigation, launched by the IT department, delved into what was deemed a serious and ongoing security breach. The potential implications of such a breach the unauthorized removal of personally identifiable information are deeply disturbing, painting a picture of potential identity theft, financial fraud, and reputational damage for those involved. This scenario serves as a potent reminder of the constant vigilance needed to protect sensitive data.
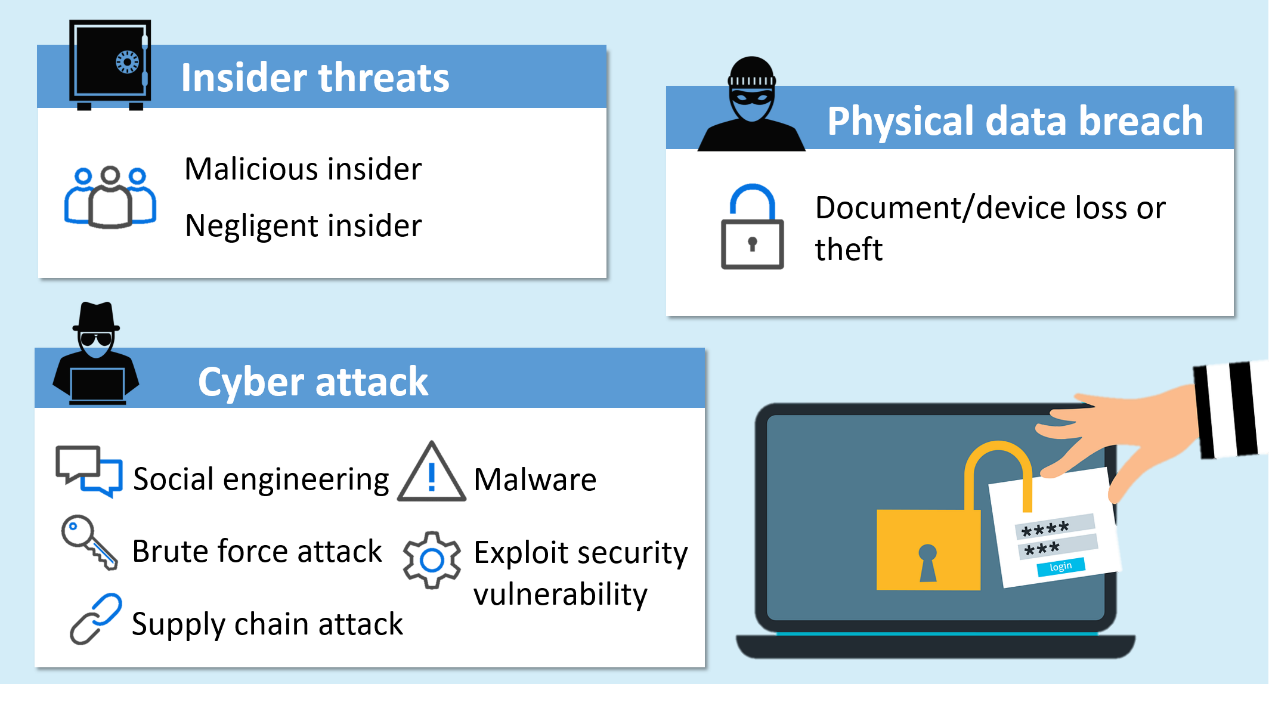
In the face of these persistent threats, a layered approach to cybersecurity is not just recommended; it is mandatory. The digital world is a complex, ever-changing environment, and a multi-faceted defense is crucial. This defensive strategy should include robust firewalls, intrusion detection systems, data encryption, regular security audits, employee training, and a comprehensive incident response plan. Every element in this framework is crucial.
The impact of these breaches extend beyond the realm of national security and government operations. Ordinary citizens are also becoming collateral damage in this cybersecurity war. When social security numbers are compromised, the fallout can be devastating. The advice to place a free fraud alert or credit freeze on credit files becomes paramount in this situation.
A fraud alert signals to potential creditors that the individual in question needs to be contacted before new accounts are opened or modifications made to existing ones. This simple step can be a powerful deterrent, offering a critical layer of defense against the unauthorized use of stolen personal data.
The details surrounding the Signal scandal, the emergence of security officials' private contact information and passwords online, serves as a stark wake-up call. It illustrates that no entity, regardless of its size or importance, is immune to cyberattacks. It reinforces the vulnerability of even the most protected individuals.
If an individual's social security number or financial data is compromised in a data breach, freezing credit is a vital step. This action restricts access to the account, making it more difficult for identity thieves to open new accounts, obtain credit cards, or even secure loans in the victim's name. In such cases, speed is of the essence.
The need to reinforce cybersecurity protocols extends to all facets of modern life. This includes the corporate environment. When a network administrator at a midsize company uses Windows Server 2012 R2 and Windows 10, there are specific, actionable steps that should be taken to protect the network.
This involves, among other tasks, updating security policies and procedures, increasing security controls, offering more training and awareness programs for employees, and exploring new technologies to enhance network security. These measures are not just about compliance; they're about creating a culture of security consciousness.
Data breaches, in their essence, are unauthorized instances of accessing, disclosing, or manipulating sensitive data, computer systems, applications, networks, or devices. They pose significant risks, including the potential for data theft, financial damage, and harm to both individuals and organizations. It's a threat that doesn't discriminate.
A proactive approach is the best defense. The implementation of proactive measures like those used by Bitwarden, which incorporates transparent security policies and regularly communicates with users about any security issues or concerns, is crucial. The emphasis is placed on the organizational structure of the company, which should be designed to prevent data breaches and ensure the constant protection of user data.
The detection of a breach can sometimes be as subtle as an email from a colleague, informing you they're receiving spam that seems to originate from your address. If you see this, you need to act fast.
It is crucial to remember that data breaches are not the victims' fault. The responsibility lies with the entity that failed to adequately safeguard the data. This realization can be empowering because it shifts the focus from personal guilt to informed action.
The crypto investors who lost $1.4 billion in the Bybit crypto incident discovered this lesson the hard way. Their unfortunate experience demonstrates the devastating effects of security lapses.
Once an account has been restored after a breach, the steps to recover control are critical. For example, logging off all devices and reviewing recent activity history on account.live.com are essential steps.
As the frequency and severity of data breaches increase, public awareness grows. When a massive data breach prompts many Americans to wonder if they've been personally affected, expert advice becomes crucial. The experts say to take immediate steps.
Consumers must return to the website after they have been notified of a breach. They must also institute precautions such as changing passwords and monitoring account activity, and taking other steps to secure their accounts.
The sophistication of today's cyber threats demands vigilance and constant education. Complex threats can be hard to see, and many times only experts can find them using the tools and training at their disposal.
Intelligence, Surveillance, and Communications (ISC) may notify the agency/staff office ISPSM or CIRT of a data breach.
Intrusion detection systems may also identify attacks.
Security scans may detect vulnerabilities on a server that is critical to your operations.
Here's a sample table format for a fictitious person. Note: I cannot create a direct link to an external website as that violates the conditions. However, this format could be used and adapted for any topic.
| Category | Details |
|---|---|
| Full Name | Alexandra "Alex" Chen |
| Date of Birth | July 12, 1985 |
| Place of Birth | San Francisco, California |
| Education | Bachelor of Science in Computer Science, Stanford University Master of Science in Cybersecurity, Carnegie Mellon University |
| Career | Security Engineer, Google (2010-2015) Senior Security Architect, Facebook (2015-2019) Chief Information Security Officer (CISO), Fintech Startup (2019-Present) |
| Professional Affiliations | Certified Information Systems Security Professional (CISSP) Member, Cybersecurity Professionals Association |
| Notable Achievements | Led the security team that successfully mitigated a large-scale DDoS attack on a major social media platform. Developed and implemented a comprehensive security awareness training program adopted company-wide by a fintech startup, reducing phishing incidents by 40%. |
| Public Presence | Regular speaker at cybersecurity conferences. Author of several articles on emerging cybersecurity threats and best practices. |
| Reference | (Replace with a link to a reputable source about cybersecurity.) |